What are HIPAA disaster recovery requirements? Healthcare data breaches exposed over 276 million patient records in 2024, representing more than 80% of the US population according to the HHS Office for Civil Rights. For healthcare organizations, the question is no longer whether a disruption will occur, but when. The HIPAA Security Rule addresses this reality directly through its contingency planning requirements, yet many organizations still operate with significant compliance gaps.
Understanding what HIPAA actually mandates for disaster recovery helps organizations build compliant, practical recovery capabilities without overengineering or underpreparing.
What HIPAA Requires for Disaster Recovery
The HIPAA Security Rule’s contingency plan standard (§164.308) establishes five implementation specifications. Three are required, and two are addressable.
Required specifications include a data backup plan that creates retrievable exact copies of electronic protected health information (ePHI), a disaster recovery plan with procedures to restore any loss of data, and an emergency mode operation plan that maintains critical business functions while protecting ePHI security during a crisis.
Addressable specifications cover testing and revision procedures for periodic plan evaluation, plus application and data criticality analysis to identify which systems need priority restoration. While “addressable” doesn’t mean optional, it does allow organizations to implement alternative measures if they document their reasoning.
The rule intentionally avoids prescribing specific technologies or recovery timeframes, giving organizations flexibility to design solutions appropriate to their size and complexity. However, this flexibility also creates confusion about what constitutes adequate compliance. According to the HIPAA Journal, covered entities must be able to restore ePHI to its original state after any type of disruption, whether from ransomware, hardware failure, or natural disaster.
Common HIPAA Disaster Recovery Compliance Gaps
Most healthcare organizations have some form of backup in place, but backup alone doesn’t satisfy HIPAA’s disaster recovery requirements. The gaps typically appear in three areas.
Untested recovery procedures: Many organizations back up data regularly but have never actually tested a full restoration. When the Office for Civil Rights investigates a breach, they examine whether contingency plans were tested and revised. A backup that can’t be restored quickly or completely creates compliance exposure and operational risk.
Incomplete emergency mode planning: The emergency mode operation plan requires documented procedures for continuing critical business functions during an outage. This goes beyond IT recovery to include communication protocols, manual workarounds for patient care, and clear role assignments. Organizations often have IT disaster recovery plans but lack the operational continuity component.
Missing criticality analysis: Without a formal assessment of which applications and data are most critical to patient care and business operations, organizations can’t prioritize recovery efforts effectively. This analysis should drive decisions about recovery time objectives (RTO) and recovery point objectives (RPO) for different systems.
The Real Cost of Inadequate Disaster Recovery
Healthcare downtime carries significant financial consequences. Research from the Ponemon Institute indicates healthcare organizations lose an average of $7,900 per minute during system outages. For medium-sized hospitals, a one-hour EHR outage can cost $1.7 million; large hospitals face losses up to $3.2 million per hour.
Beyond direct financial impact, the IBM Cost of a Data Breach Report 2024 found healthcare breach costs average $9.77 million per incident, the highest of any industry for fourteen consecutive years. OCR enforcement activity increased substantially in 2024, with 22 HIPAA investigations closed with financial penalties.
The operational impact extends to patient safety. EHR outages can delay treatments by up to 20 minutes, and medication error risk increases by up to 30% during downtime according to healthcare IT research. These aren’t abstract compliance concerns; they’re direct threats to care quality.
Building a Compliant Disaster Recovery Framework
Effective HIPAA disaster recovery starts with the criticality analysis that many organizations skip. Identify every system that stores, processes, or transmits ePHI, then categorize each by its importance to patient care and business operations. Systems directly supporting clinical care typically require the shortest recovery times.
For each critical system, establish specific RTO and RPO targets. RTO defines how quickly the system must be restored; RPO defines how much data loss is acceptable. A patient monitoring system might require an RTO of minutes with zero data loss,
while an administrative system might tolerate several hours of downtime and a day’s worth of data loss.
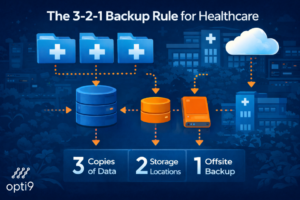
The 3-2-1 backup rule provides a solid foundation for data protection: maintain three copies of data, store them on at least two different media types, and keep one copy offsite or in a geographically separate location. For healthcare organizations facing ransomware threats, immutable backups that cannot be encrypted or deleted by attackers add an essential layer of protection.
How Veeam-Powered DRaaS Addresses HIPAA Requirements
Disaster Recovery as a Service (DRaaS) solutions built on Veeam technology address each HIPAA contingency planning requirement systematically. Automated backup verification confirms that backups are actually restorable, not just complete. Immutable backup repositories protect against ransomware encryption. Orchestrated failover capabilities enable rapid recovery to meet aggressive RTO targets.
As a Veeam Platinum VCSP Partner and 2024 Veeam Innovation Award Winner, Opti9 delivers HIPAA-compliant disaster recovery through managed services that handle the technical complexity while providing the documentation and testing evidence OCR expects during compliance reviews.
The combination of Veeam’s data protection capabilities with Opti9’s managed services approach means healthcare organizations get enterprise-grade disaster recovery without building and maintaining the expertise internally. This is particularly relevant for mid-sized healthcare organizations that need sophisticated protection but lack dedicated disaster recovery staff.
Taking the Next Step
HIPAA disaster recovery requirements exist because patient data protection and care continuity genuinely matter. Organizations that treat compliance as a checkbox exercise often discover gaps only after a disruption exposes them.
A practical starting point is reviewing your current backup and recovery capabilities against each HIPAA contingency planning specification. Can you demonstrate that backups create retrievable exact copies? Have you tested full restoration within your target recovery times? Do you have documented emergency mode procedures that staff actually know how to execute?
For healthcare organizations looking to strengthen their disaster recovery posture, Opti9’s healthcare IT resilience assessment provides a structured review of current capabilities against HIPAA requirements, with specific recommendations for closing any gaps.